In our latest Wired-In webinar, Corinna Venturi, Director of Financial Crime at Cosegic, assessed best practice KYC compliance and provide insight to create and run an effective KYC programme.
Webinar transcript
Reece Baggott, Digital Marketing Lead at NorthRow: Hello everyone, good morning and welcome to July’s instalment of Wired-In. Today, I’m joined by Corinna Venturi from Cosegic who is Director of Financial Crime.
I can still see a few people getting settled so we’re just going to give it a few minutes, do a few formalities in terms of introductions, and a bit of housekeeping before we start.
Today, as mentioned, we’re joined by Corinna who is going to be looking at best practice in KYC in 2023. I’m delighted to welcome you all as well, this session has been greatly received and we can only thank you for that.
Corinna, if you don’t mind forwarding that slide for me, please.
Just a bit of a shameless plug, if you don’t know who NorthRow are or what we do. We offer KYC, ID&V, KYB and AML compliance platforms which help you accelerate growth safely, onboard clients in seconds, not days, and also comply with ever-changing legislation. If these challenges resonate with you, head over to northrow.com, there is tons of information there but hopefully today we’re going to be ‘wired-in’ to this session with Corinna!
As you can see, our amazing guest, you should see both of our faces at the top of your screen. We’re joined by Corinna Venturi who is the Director of Financial Crime at Cosegic. Corinna joined in 2022, she’s been a financial crime consultant since 2017. Prior to that, an MLRO and Head of Compliance for one of the largest trust corporate service providers. After deciding to pivot her career from client relationship management to financial crime prevention in 2007, Corinna completed the ICA’s Diploma in AML whilst simultaneously tackling her first MLRO role. In 2012, she became a Fellow of the ICA. Tons to talk about!
But for now, Corinna, the floor is yours.
Corinna Venturi, Director of Financial Crime at Cosegic Thanks so much Reece, appreciate that lovely introduction. So, achieving best practice KYC, CDD, all of the acronyms!
So, I feel certain today that most of you listening are going to understand the concept of KYC and CDD already so we’re not going to go over the basics of performing customer due diligence. Today is about specific areas that I see are regularly misunderstood or simply not fully considered in the context of a firm’s self-assessment of their own risk.
The areas I want to cover over the next hour are the importance of matching risk appetite to actual KYC/CDD skills and experience, when and how to use manual and electronic identification and verification (so that includes things like selfies as well), effective screening and avoiding inputting errors, and then the difference between information and evidence which we’ll look at across the board but also specifically in terms of source of wealth.
Risk appetite vs. skills
Looking first at risk appetite versus skills. Relevant firms need to assess the risks presented by their customers and any underlying beneficial owners. If I’m talking about beneficial owners, I mean customers as well, so the whole thing is encompassed.
Their products and services, transactions, delivery channels and geographical areas of operations. Then they need to design and implement controls to manage and mitigate those assessed risks in the context of their risk appetite. Part of the financial crime work we do at Cosegic involves guiding our clients or conducting these risk self-assessments because all too often, it can become a bit of a phoning it in exercise. I promise you, if it’s not conducted properly, and regularly as well, it can be a really serious issue with the regulator.
Having thoroughly assessed the financial crime risks to your business, the firm can then create a meaningful financial crime risk appetite statement. If that appetite is quite high and they’re willing to tolerate a lot of risk, then they have to have compliance staff, and first-line staff. Anyone relevant to that business has to have the necessary skills and experience to meet that risk and then mitigate it appropriately.
You might wonder why I’ve put a down trend trading graph on this slide! It’s just because it makes me think of so-called unsophisticated investors. For context, if you think about a sophisticated investor that could be a high net worth investor who is considered to have a depth of experience and market knowledge that makes them eligible for certain benefits and opportunities. You’ve got institutional investors which are employees who invest on behalf of other people, and then you’ve got retail investors who may or may not know much about trading and they are individuals that invest their own money typically on their own behalf.
So an unsophisticated investor could be a retail investor who might bet their mum’s house on Bitcoin with no knowledge of the risks that they face. They base their research – in quotes – on the soundbites of their favourite Instagram crypto bro!
That downtrend graph is exactly what can happen to a firm who takes on a huge amount of fincrime risk without the knowledge and expertise to back it up.
The obvious way to understand if you’ve assessed your risks thoroughly and have implemented appropriate policies and procedures is to engage an external third party, like Cosegic, to conduct a financial crime assurance review. Sometimes you get blindness with your policies, procedures, systems and controls because you’re doing it every day, you’re looking at it and so things can get missed.
The fallout
We’ve got the fallout here, that’s what happens when a firm grows really quickly, touts their unique selling point as perhaps linking a high-risk jurisdiction with UK payments services, or promoting high-risk, high-reward investments etc. But they haven’t got the right people, and/or, the framework in place to support that.
Examples of possible fallout can be reputational risk and damage, downsizing of the business, loss of business, regulatory sanctions, financial penalties, and sometimes criminal penalties.
Over the years, there are some key areas of KYC/CDD that seem to pop up the most often as a result of the mismatch between risk appetite and skills and experience that are available within a firm. That’s what we’re going to look at now.
Verification and risk classification
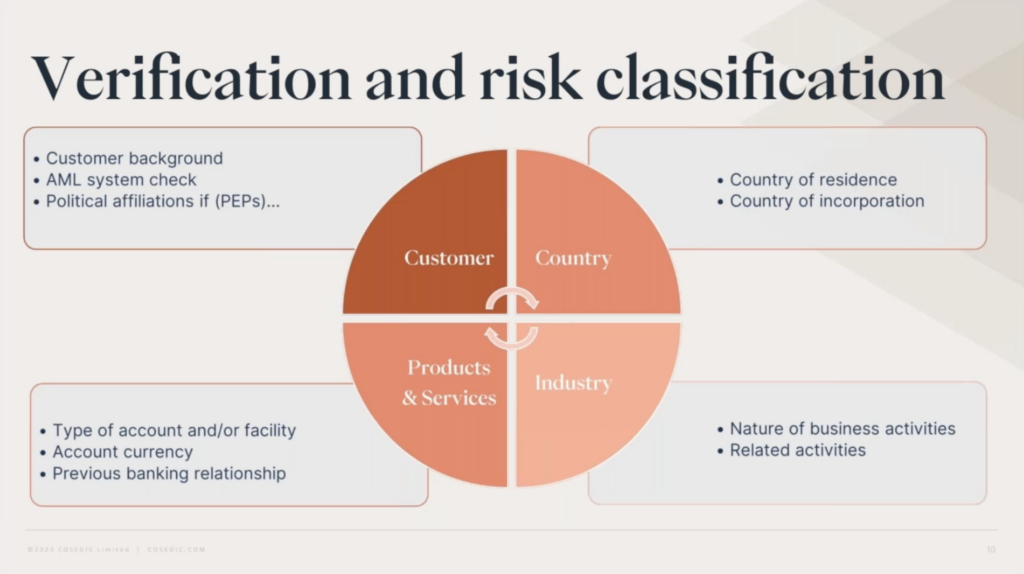
There are several ways to verify documents that identify a customer, and the level you go to has to be linked to a customer risk assessment. Without that, you could end up applying verification as a one size fits all and there are loads of possible repercussions from doing this. The key ones could be something like, if you apply enhanced verification across the board resulting in additional time and resources on every single customer, you could be annoying the customer, being really inefficient as well, all that time and money being spent when you don’t necessarily have to. Conversely, if you did the opposite and applied a light touch verification across the board when all your customers wouldn’t be considered low risk, then you’d be open to missing flags.
Verification methods
Here, I’ve just put up some of the methods of verification that can be applied. Again, how you do that as a firm depends on so many factors. That’s what makes it so fun! What type of customers you have, how many, how much money do you have to spend on automation, and things like that. That can only be assessed from a risk self-assessment of the business, not the customer, to get a true understanding of the intended business, how fast you plan to expand, the ability of staff to ensure whichever verification method that is used is being used correctly.
I’ve put the key ones up on the slide. Up top, we’ve got in person. Fabulous, if you can do it. You can eyeball that customer, visit the premises, match the original ID docs to the person that is standing in front of you. But in today’s world, this method is increasingly uncommon due to the time and resources spent on having to do it. However, if that customer is potentially very high risk, perhaps you’d consider it as part of the method employed to mitigate that risk.
You wouldn’t necessarily employ this method for every single customer, again, depending on your business. If you’re a business that has very few customers, a very small number of high net worth individuals, it might be totally worth it and make sense to do it that way. In fact, in that kind of business, maybe that’s the normal way to do it. A more traditional approach I suppose.
If you’re going to do in-person, it’s not just enough to visit that person and say “Yep, that’s great, done that, seen that!” You’ve got to record it properly. Often I see missing evidence of this on customer files, it might say in an onboarding form ‘visited premises’ or something like that. But then there is no record. When did you do it? What did you do there? What did you see? Unless you record it, it just hasn’t happened and it is always about the record. You can’t prove what you’re doing without properly documenting it. And it needs to be on the customer file or at least linked to really clearly. Because another thing we see all the time, particularly when we’re reviewing customer files, we’re doing sample reviews, is that the information is all over the place. So we get a customer file, typically electronically, but key data like this is held in other systems so it can be really difficult to review. If a regulator is coming in, or an enforcement agency is coming in, they need to see all these things in one place.
Next, we’ve got manual certification. You might have a medium or high-risk customer and you can’t meet them in person but you want a bit more comfort that the copy documents they’re sending aren’t fraudulent. You can get that comfort from a suitable professional that the customer has access to. That professional, could be a lawyer, an accountant for example, sees the person and the original documents and then certifies on those copies that this happened and everything is in order. That one only works if the certification contains all the necessary information. You’re going to want to see the name of the person, their profession, their title, the business they work for, the professional body they’re a member of, an address, maybe a telephone number, and of course, the wording has to really clearly say what they’ve done. “I’ve seen the originals, and this is a true copy of those.” If it’s a photograph of someone, like a passport, then the photo matches the person that was standing in front of them. Again, a lot of the time, that is missing. It’s “this is a true copy.” Great! It’s a little bit light touch, does it give you everything? Are you able to check the certifier from that information?
Next, we’ve got electronic sources so that is good for firms with larger customer bases with a high proportion of low or medium risk compared to their high risk. Not always larger firms, we’ve got so many options now that lots of different firms can use electronic verification systems. Electronic sources can be lots of different things, not just verification software. You can use automation to speed up processes and shift resources where they need to be. Using electronic sources doesn’t just mean automation software either, it can include selfies, so photographs of someone holding their passport so you can actually see and match it up. Even things like looking online, looking at a customer’s social media profile, anything that a KYC analyst can access that helps build a picture, a profile of that customer to support their ID claims. This one only works if the electronic sources that you or your provider use are robust and make sense for that particular risk level.
I put hybrid at the end because you can use any and all of these across your customer base and even across a single customer. If you’ve got a customer that is high-risk or very high-risk, it’s probably not going to be appropriate to only apply electronic verification on, say, self-reported ID data points. But you might run those data points through your software and have that supported by a selfie, for example. There are different ways that you can be doing this.
Electronic verification

I’ve just put up this on the screen, I’ve lifted this straight from the Joint Money Laundering Steering Group guidance part 1. I put that up just because it’s really important to make sure you’re using electronic verification tools and AML software tools properly, and you’re able to demonstrate that they’re fit for purpose. Does the report that the user gets tell a good enough story about that customer? Is the person or company who they say they are and how can you be sure? You’ve got to be thinking about this. Does it make sense? Does the tool work in the way you need it to?
Effective screening
Again, like the electronic verification tools, a screening tool also needs to be fit for purpose and able to be used properly in order to be effective. This is another area where I see firms feeling pretty happy with themselves because they’ve spent a ton of money on a full bells and whistles screening system to screen for PEPs, sanctions, and perhaps also adverse news a lot of the time now, but no one in the firm really understands how to use it to its fullest capability or the settings are such that they’re getting so many alerts they don’t have the resources to process them. This comes down to the firm’s risk self-assessment and due diligence in choosing a provider. Assessing your business and its explicit needs determines which resources are utilised, but of course, your screening software doesn’t work on its own. It needs to be configured to suit those needs and then have appropriately skilled users to assess the data that it ends up spitting out. In the beginning, real care and attention has to be spent choosing the right provider, understanding how the tool can best suit a business’ needs. But it doesn’t stop there, the system has to be configured properly and regularly tested to make sure that the settings continually align with the business’ customer base and external factors such as changes in legislation and things like that.
A lot of the time, the software provider can help with this and they are usually really happy to help with configuring, fuzzy settings, or just answering any questions that you’ve got. Do make sure that you are interacting with them regularly if you need to.
A system is only as good as it’s user so the person or people tasked with monitoring the output from such a system needs to be properly trained, and they need to understand how to put the least data in whilst getting the most out of the results, and not getting a bunch of false positives that they then have to spend hours or days wading through. It completely defeats the object.
Most modern screening tools have pretty sophisticated search settings which allow for differences in spellings of names and user inputting errors, however the more a user can be precise or you know use certain versions of the name where necessary, the less chance of missing something. You’d be surprised but another thing I see too often is utilisation of a screening system, setting a manual search to ongoing, so you’ve done that initial work, you can turn it on to ongoing so it continually screens for the life of the customer relationship. But then never checking the case manager or processing the alerts, so that turns your state of the art screening system into a completely pointless added expense.
If you’re getting so many returns that the relevant person or team can’t handle them, then either there is a problem with the settings which can be usually pretty easily fixed, or there is a resourcing issue or it could be a combination of both of those things. That is something that can be brought up with senior management and resolved. It’s really important, there’s no need to turn a blind eye and say ‘hey, we’ve got this really great system, box ticked!’
I’ve also added here, help out your screening provider. They’re not perfect, nobody is, nothing is and on a few occasions over the years, I’ve seen on publicly available sources that a person is clearly a PEP or has serious adverse news about them but they don’t come up in the screening tool. If you see this, don’t ignore what you’ve seen and take the report as read. You can gather your source references and send these to your screening provider and they’ll analyse this and determine for themselves whether or not to add or update a report. I’ve also reached out to update the software provider with information based on information I’ve found publicly or by sharing documentation sourced directly from the customer, with their permission of course.
Usually, the latter I am referring to legal issues that have actually been resolved but not updated on the screening report. This is great for you as well because you’re not having to add to your customer file a report that says ‘no they’re not a PEP’ but then you’re trying to add to the case that they are. It’s great if you can get it updated or at least having your software provider’s second set of eyes looking at it as well so you’ve got a little bit of comfort there. It’s a two-way street so use that option, for sure.
Information vs. evidence for KYC compliance
The final area that I see regularly misunderstood or inadequately recorded is around the collection of information versus the evidence to support that information.
Once again, how and what you collect in terms of piecing together that picture of your customer is determined by the level of risk that they pose. For the purpose of this point, I’m going to focus on higher risk customers and enhanced due diligence because those are the juicy ones, the ones that can be really tricky.
You can see on the screen on the left-hand side that information is just the data points. So when you’re talking about information, it’s the data points provided to you to identify the person or company that wishes to do business with you. That can be collected on an interactive webform, or in-person by a member of the sales team, or some other way, however you guys each do it. It’s useful but it’s just information, it’s your starting point. Collecting information doesn’t address potential risk of impersonation fraud. What does mitigate this risk is collecting supporting evidence and that links back to verification too. There’s some intricate crossover between evidence and verification that’s important to understand.
Let’s say, for example, your potential customer fills in a form with their ID data points in it and then they send you a blurry copy of a passport by email to support those data points. Does that pass for verifying those ID data points? Does it evidence them?
What if they send instead, a clear selfie of themselves holding the passport and you can see the information and the photo likeness of them and it looks like the person holding it. Does that do the job? Is that proper evidence? Is it proper verification?
If a non-UK company sends you all of their statutory documentation by email, and there is a certification on each document and it states the certifier’s name and address, and a statement that says they’ve seen the original and this copy is a true copy. Does that verify those documents are genuine?
You’ve got to be thinking about this all the time and not just going ‘we’ve got this information, here’s a bit of paper.’ You’ve got to be thinking about what it means in reality. Does it really evidence it? Is someone trying to pretend to be someone else? What you’ve got in front of you, what you’ve been provided, does that strongly mitigate that risk?
Source of wealth: Information vs. evidence for KYC compliance
Specifically with the source of wealth information versus evidence, it’s not just about those ID documents. Source of wealth, nature of business can be really tricky to evidence sometimes. Again, hoping that you’ll have questions about that because it is the thing I get asked about so much. How do we do it? I think the reason is because it’s hard to be prescriptive about it, there’s an art to it in a way which is not that helpful when you’re trying to do things the right way or trying to ensure the regulator is happy. Saying that it’s artful can sometimes not be that helpful! You’ve got to think of it more holistically and look at the bigger picture and what you’re trying to achieve.

I’ve just put a few examples here, but obviously there are tons of different sources of wealth and things like that but they’re just things that come up quite regularly.
On the left, the information is simply a description of the source of wealth. Here, all you’re seeing are very brief descriptions, a couple of words and that’s already a problem and one that would need addressing. For inheritance, who is it from? Do you need to know the source of their wealth, the person it came from? They’re not around any more so how do you find that out if you do need to know it? But it’s that flow of funds. If it’s the proceeds of crime, you do have to get a little bit more information.
Same with the beneficiary of trust funds. Does that trust have a corporate trustee? Do you need to understand the settlor source of wealth because you’re looking at that money flow.
Looking at consultants as well, is that a well described source of wealth? Obviously not. What industry are they in? How much do they earn? Where do they perform their services et cetera?
Dividends from a person’s own business. This is an interesting one, and I would be really interested to hear people’s thoughts on this but I’ve seen that quite often as being a source of someone’s wealth. Is that actually their source of wealth? Or would it be the money that they used to initially fund the business? Now it might be but where did they get the money from originally? What if that was the proceeds of crime and they’ve legitimised it by creating a legitimate business? Can you take that at face value? If it’s a business that had external investors, do you need to understand anything about that? As I said a couple of slides ago, I’m looking at high-risk type customer relationships and where you might really be thinking about digging deeper and understanding.
In my previous life as an MLRO in the trust and corporate services world, I cannot tell you how many times I saw entrepreneur used to describe source of wealth. Like a consultant, it tells you absolutely nothing, so when requesting source of wealth in the first instance, it’s always important to guide your customer on how to answer the question.
Often, they may genuinely just not know the level of detail that you’re looking for. It’s really important to tell them, explain to them, describe on your forms and hand-hold them. That saves you time and energy as well, and it helps you decide quickly what you might need to find out.
I’ve just put the evidence here, potential evidence, it could be lots and lots of things. For example, inheritance. Can you have a copy of the will? Information from the executor? Source of wealth of the testator? How would you do that if they’ve passed away? Who is going to be able to give you that information?
All of these are real examples that we’ve had to look at. When we’ve started off looking at the testator and background checking their names, if nothing comes up that’s really negative, you might feel like you could stop there depending on level of risk.
If something comes up that looks a bit fishy or looks like it’s going to need more, then you’re going to be going to that executor or whoever and trying to find out more information.
Consultants, you could maybe get their bank statements, wage slips, do they have a website? Is there presence? That’s another thing that would be important to think about is websites. Really easy to set up websites. Most people only check the first page of Google because we’re rapidly looking through. I have also seen examples of where someone has been trying to look as though they’ve been around for a long time, look as though they’ve got a lot of substance to their business but actually they had hired somebody to create a load of pages that came up on the first and second results pages of Google. There are companies that will do that so you’re also battling against that when you’re thinking about substance, you’ve got to have a look.
The reason this popped out as being unusual to us when we were looking at it was that all of the websites only had a front page. And then each of those front pages when you clicked in just had the same information on it, so it hadn’t been done very well. With that, it’s just popped into my mind just now, you have to think about AI as well. We’re using AI, we’re using the tools of AI to help us combat financial crime. This was a long time ago when this particular case happened and it was easy to spot because it was human, and maybe a little bit lazily done. But with AI doing something like that, they can create something much better and much harder to spot. It’s important that you’re thinking of that as well and, if that’s a risk to your business, do you have the right tools on your side to combat that?
Trusts can be really tricky as well. Trust ownership and things like that. Especially offshore trusts, again you’re looking at money flows. Even though the trustee is the legal owner of the asset, it’s the settlor that put those assets in, and has maybe fed in funds or property or whatever it might be. You’ve got to consider the right parties that you’re performing your due diligence on.
Dividends from business, as I said, once you’ve figured out if that is actually enough. If it was, do you want to see bank statements, financial statements of the company, dividend certificates and things like that? Again, entrepreneur, consultant, you can be thinking about the same things but I’ve added on professional references here which can be utilised across the board. But with those professional references and certifications, you’ve got to, in higher risk circumstances, be checking those as well.
Independently checking, independently searching for their membership to a professional body for example. Is it who they say they are? Anyone could write anything on a copy documents and sign it to say that they’re a lawyer. Or pinch the details from the internet for example. You’ve got to look out for these things, use a risk-based approach and always think about this enhanced due diligence.
Beyond box-ticking in KYC compliance
Circling back to the main point of this webinar, I just want to talk about box-ticking. Much maligned box-ticking! People now tend to talk about ticking boxes as a really terrible thing all the time. Let’s not forget it’s part of the process of creating and maintaining good compliance practices. However, if you want to achieve best practice in KYC, CDD, it’s really important to go beyond it. The box-ticking, don’t forget it because it creates that solid framework for you as practitioners to work from, and customers to provide information against. Beyond that, is creating genuine understanding of what that data actually means. What use it’s intended for and whether it really does the thing that you want it to do which is to tell you whether the person or the company that wants to do business with you is genuine and wants to use you for appropriate purposes.
That’s what it is always about. Sometimes we can get mired in the documents and the box-ticking, have I followed this, have I got this bit of paper, or this piece of information, without looking at it holistically. You’ve got to look at the whole process all the time, does it make sense? You’re always linking back to your business’ fundamental risk appetite, is this the sort of thing we want to be doing? What are the repercussions if we do it and it doesn’t work out?
So, that is the end for me, if you’ve got any questions on that.
Reece B: Amazing, thanks Corinna, that was great. I’m sure a lot of people found it insightful as well. We had a few thoughts come in as well when you were talking about source of wealth, around the evidence. For example, someone said: “Best to get evidence from more than one source,” so people shared their input which is great to see.
We have had a few questions come in, a few that I’ll forward offline as well that are a bit more for Corinna to go a bit more in-depth.
This is quite a long one Corinna but we’ll start with this one: “How would you adopt an effective CDD programme for a debt purchaser where the company would not onboard each customer but purchase a portfolio of accounts from a lender and still be required to conduct CDD and ongoing monitoring. The information they have obtained could be historic and therefore impact screening reliability.” Quite long but any thoughts around that?
Corinna V: That would be quite a long answer as well, how to put in a CDD programme for something like that. Really interesting business type as well! You’re buying a book of debt, cut price and then you’re going to have the information, the due diligence around the people that have the debt but you’ve also got the company that it comes from. So, it would be important to understand the type of business it’s been bought from first of all, and the due diligence that has been done on that company. I’m not sure I can answer that because it is quite a long answer in this session, purely because of the type of business it is as well. It’s a little bit unusual, it would be good to get a bit more information from whoever asked that actually. Is there anything more specific about it that you’re wondering about.
Reece B: Sure thing, we can take this offline and forward their details to yourself. If anyone is going through a situation similar, please do connect with Corinna on LinkedIn as well.
Another one of the questions we’ve had is: “What are some of the key metrics or indicators you’d recommend to assess the effectiveness of a KYC programme?”
Corinna V: You’ve got to have a look at any sort of monitoring that’s happening. When we do our assurance reviews, we’re going through the best indicators are the customer files. That’s really what’s happening in practice, going through each one of those and lining up against the requirements, looking at the customers, the transactions, products, services, all of the things that are on your risk self-assessment basically. These are the things that we measure against very carefully.
Reece B: Awesome. We’ll just go for one more after that: “How would you balance the need for stringent KYC processes with providing a positive customer experience?”
Corinna V: I think that harps back to my point about the verification and using that risk-based approach because it’s really easy to get a little bit scared and go ‘okay, we’re just going to over apply our processes on the customer’ and that’s just not going to work. You’ve got to be so careful, and it’s a great question because it’s everything that we’ve just been talking about. Effectively, you’ve got to treat them all on their own merit. If you’ve got a book of thousands of customers, you’ve got to be using your data about your own customers and types of customers that you’re targeting to understand where you can do a little bit less and where you can do a little bit more.
You’ve got to have a really strong customer risk assessment in place so that you can properly categorise them, so you’re viewing your lower risk customers properly and you’re not overdoing it and annoying them. With the higher risk customers, you can spend more time. And there’s the balance. If you apply that enhanced across the board, you’re going to lose a lot of customers because they’ll go somewhere else because they know that that’s too much information and it’s taking too long to open an account or whatever it might be.
Reece B: Amazing, we have had another one come in as well but I’m going to forward that on to Corinna as it’s a bit of a long one.
I think we’ll wrap that up for questions so if you don’t mind forwarding the slide for me please?
So, about the Wired-In series. It’s normally a monthly series that we host. We gather thought leaders from Fin and RegTech to explore topics like Corinna has done today to help with your day-to-day practices. You can check out our archive over on the NorthRow website and you can watch out for the next which is going to be just shy of a month away. Keep an eye out for emails coming out.
I know we talked about NorthRow a little bit earlier, but if you would like to find out more, you can head over to our website but there’s tons of information there about how we can help you with AML compliance through onboarding, monitoring and remediation.
But that’s enough from us today! And I think that brings us to a close. Thank you so much Corinna for an amazing session, if you do want to connect with her, go over to LinkedIn. We’ll include details in the email with the recording and do go and check out Cosegic as well, they’ve got some great stuff over there, highly recommended!
A massive thank you to everyone that has joined us today, a massive thank you to you Corinna and we look forward to seeing you on the next one.
Corinna V: Thanks so much.








